A cybersecurity risk assessment template is your roadmap for systematically finding, measuring, and prioritising digital threats. Think of it less like a checklist and more like a strategic game plan. It is the tool that helps you shift your security posture from constantly putting out fires to proactively preventing them in the first place.
Building Your Cybersecurity Defence Strategy

Before diving into spreadsheets and scoring systems, it is crucial to see this template for what it truly is: the bedrock of your entire defence strategy. This is not just about satisfying a compliance requirement. It is about creating a living document that makes your organisation genuinely more resilient to the threats we see every day.
This proactive approach is more important than ever, especially when you look at what is happening locally. In 2025, for example, Australia saw a staggering rise in cyber incidents. Phishing attacks doubled in just nine months, with attackers using sophisticated AI to make their scams more convincing. Ransomware also hit hard, with one in three Australian businesses suffering multiple attacks within a single year. These numbers drive home the urgent need for a solid, repeatable assessment process.
Shifting from Reactive to Proactive
A well-designed template fundamentally changes how you think about security. Instead of scrambling to respond after a breach, you start to anticipate where the next attack might come from. This proactive mindset is built on a few core pillars, which should form the key sections of any good template:
- Pinpointing Critical Assets: What data, systems, and hardware are absolutely essential to your business?
- Analysing Potential Threats: Who might target you and what methods would they use?
- Spotting System Vulnerabilities: Where are the weak spots in your technology, processes, or even among your people?
- Planning Mitigation Controls: What is the action plan to reduce or get rid of the risks you have found?
To get this right, you need a solid grasp of the fundamental risk management principles that form the foundation of any effective security programme.
The real power of a risk assessment is not the final report. It is the conversations and decisions it sparks. It gets everyone—from IT to the C-suite—to agree on what is most important and where to spend your limited security budget for the biggest impact.
A solid template should break down these pillars into manageable parts. Here is a quick-reference guide to what those core components look like in practice.
Core Components of a Risk Assessment Template
| Component | Objective | Key Action |
|---|---|---|
| Asset Inventory | To know what you need to protect. | Catalogue all critical hardware, software, and data assets. Assign ownership and business value to each. |
| Threat Identification | To understand your potential adversaries. | List relevant threats, such as ransomware, phishing, insider threats, and system failure. |
| Vulnerability Analysis | To find your weak points. | Scan for software vulnerabilities, assess process gaps, and identify areas needing staff training. |
| Impact & Likelihood Scoring | To prioritise what matters most. | Evaluate the potential business impact of a breach and the probability of it occurring. |
| Risk Register | To create a central source of truth. | Document each identified risk, its score, current controls, and a recommended action plan. |
| Control Implementation | To actively reduce risk. | Define and assign specific technical or procedural controls to mitigate high-priority risks. |
This structure ensures you cover all your bases, turning a daunting task into a methodical process.
The Importance of Customisation
No two organisations are the same, and neither are their risks. A generic template you download online is a great starting point, but its real power is unlocked when you tailor it to your specific industry, business operations, and compliance needs.
This customisation is what turns a basic document into a sharp, effective tool for making smart, informed decisions. For more on weaving security into your day-to-day operations, you can read our insights on https://redwolfrosch.com.au/blog/tech-and-cybersecurity-for-business.
Mapping and Valuing Your Critical Digital Assets
Let us start with a foundational truth: you cannot protect what you do not know you have. The entire cybersecurity risk assessment process hinges on this first, critical step—building a complete inventory of your digital assets. And I am not just talking about a quick list of servers and software. This is about digging deep to uncover every single piece of data, intellectual property, and system your business truly depends on.
A good asset register is more than just a list; it is a living document. For each item, you need to capture what it is, where it lives, who owns it, and—most importantly—what it is actually worth to the business. This exercise forces you to see your operations in a new light, connecting the dots between the technology you use and the core functions that keep your doors open.
Beyond the Obvious: What to Actually Include
To make sure nothing slips through the cracks, it helps to think in categories. Your inventory needs to be a whole lot broader than just the physical hardware you can see and touch.
- Data Assets: Think about your customer databases, all your financial records, sensitive employee information (PII), and any proprietary research or trade secrets.
- Software and Applications: This is everything from the big stuff, like your core ERP system, down to the custom-built tools your teams rely on, and even cloud services like your CRM or marketing platforms.
- Hardware: Of course, you need to document servers, laptops, and network gear. But do not forget any specialised operational technology (OT) that is essential for manufacturing or service delivery.
- Intellectual Property: What about your source code, unique design files, patents, or confidential business strategies? These are often the crown jewels.
Getting this part right is everything. If your asset inventory is incomplete, your entire threat analysis will be built on a shaky foundation, leaving you with dangerous blind spots you will not see until it is too late.
Assigning a Business Value to Your Assets
With your list in hand, the next job is to assign a value to each asset. This is not about slapping a dollar figure on everything. It is about understanding the real-world impact if that asset were to be compromised, corrupted, or simply unavailable. The classic way we measure this is by looking at the CIA triad: Confidentiality, Integrity, and Availability.
Let us make this practical. For a fintech company, the customer database has an astronomical confidentiality requirement. A breach there would not just be embarrassing; it would trigger massive fines under Australian privacy laws and evaporate customer trust overnight. On the other hand, a manufacturer’s proprietary design files have an incredibly high integrity value—if someone modified them without authorisation, it could completely wreck product quality and even create safety risks. For an e-commerce website, availability is king. Every hour it is down is another hour of lost sales.
Assigning a business value to each asset is non-negotiable. It is what turns a long, technical list into a prioritised roadmap. This is how you ensure your security budget and your team's effort are laser-focused on protecting what genuinely matters most. It is what elevates your risk assessment from a simple technical checklist to a powerful strategic tool for the business.
Uncovering Threats and Identifying Vulnerabilities

Now that you have a solid inventory of your critical assets, it is time to figure out what could actually harm them. This is the core of threat analysis—a process that sounds complex but is really about connecting the dots between potential attackers and the things they want to steal or break. It is all about painting a realistic picture of the dangers your organisation is up against.
Let us put it this way. Knowing you have a valuable customer database is one thing. Realising that organised cybercriminals are actively hitting businesses in your sector with sophisticated ransomware is something else entirely. That context changes everything. It turns a vague worry into a specific, tangible problem you can start to solve.
Decoding the Threat Landscape
Not all attackers are the same. They come in different shapes and sizes, each with unique motivations and playbooks. Your cybersecurity risk assessment template needs to capture this reality.
You will typically run into a few common types:
- Organised Cybercriminals: These are the pros. They are in it for the money and possess serious skills, running large-scale ransomware campaigns, stealing data to sell on the dark web, and pulling off complex financial scams.
- Malicious Insiders: This might be a disgruntled employee out for revenge or someone looking to make a quick buck by selling sensitive company data. Their insider access makes them an especially tricky threat to handle.
- Accidental Insiders: A well-meaning staff member who clicks on a phishing link or accidentally misconfigures a cloud server can cause just as much damage as a malicious actor. Never underestimate the human element.
- State-Sponsored Actors: While less of a daily concern for many SMEs, these groups are a serious threat if you are in their crosshairs. They target organisations for political espionage, intellectual property theft, or to disrupt critical infrastructure.
Figuring out who might target you is the first step to anticipating how they will do it. Their attack methods are always evolving. A perfect example is Business Email Compromise (BEC), where attackers impersonate an executive to trick an employee into wiring funds to a fraudulent account. It is simple, but devastatingly effective.
According to CyberCX's 2025 Threat Report, BEC was the number one cybersecurity incident in Australia during 2024. What is truly alarming is that 75% of these attacks got straight past multi-factor authentication (MFA), which shows just how sophisticated these threats are now. You can dive deeper into these Australian threat trends in the full CyberCX report.
Pinpointing Your Vulnerabilities
Once you have got a handle on the external threats, you need to turn the spotlight inwards to find your own weaknesses—the vulnerabilities they could exploit. A vulnerability is simply a gap in your defences that an attacker could use to get in or cause damage.
A threat without a vulnerability to exploit poses little real risk. It is the combination of the two that creates the perfect storm. Your job is to find and patch your vulnerabilities before an attacker finds and uses them.
This part of the process demands an honest, thorough look at your organisation. Vulnerabilities do not just live in your tech; they can be found in your processes and your people, too.
- Technological Vulnerabilities: These are usually the most obvious culprits. We are talking unpatched software, old operating systems, poorly configured firewalls, or insecure cloud storage buckets. Running regular vulnerability scans is an absolute must-do for finding these gaps.
- Process Vulnerabilities: Weaknesses can also be baked right into your daily operations. Maybe you lack a formal incident response plan, do not properly vet the security of your vendors, or have sloppy data backup procedures. These are vulnerabilities waiting to be exploited.
- People Vulnerabilities: The human element is often the weakest link in the chain. Gaps in security awareness training make your team a soft target for social engineering, while weak or reused passwords are like leaving the front door unlocked.
By systematically documenting these threats and vulnerabilities in your template, you are building the foundation for the next stage. This context is essential for accurately scoring risk and, ultimately, making smart decisions about where to focus your defensive efforts.
Calculating Risk and Prioritising Your Action Plan
This is where the rubber meets the road. All that groundwork identifying assets, threats, and vulnerabilities now comes together to become a practical, decision-making tool. We are moving from a general awareness of what could go wrong to a clear, data-informed plan for what to fix first. The whole point is to systematically calculate risk so you can spend your time and budget where it matters most.
The most common way I have seen this done—and it is effective—is by combining two key factors: the likelihood of a threat successfully exploiting a vulnerability, and the potential business impact if it does.
A simple multiplication of these two gives you a risk score. Suddenly, you have a clear hierarchy. A low-likelihood, low-impact event? That is a minor concern. But a high-likelihood, high-impact event? That is a code-red priority demanding immediate attention.
From Scoring to Strategy
Once you have got those individual scores, the next step is to map them onto a risk matrix. Think of it as a visual dashboard for your risk landscape. It typically uses a traffic light system (Red, Amber, Green) or labels like High, Medium, and Low to rank every risk you have identified. This is brilliant because it translates raw numbers into a strategic guide that anyone, from the tech team to the board, can understand at a glance.
This diagram helps visualise how all the pieces—asset identification, threat assessment—feed into that final calculated risk score.
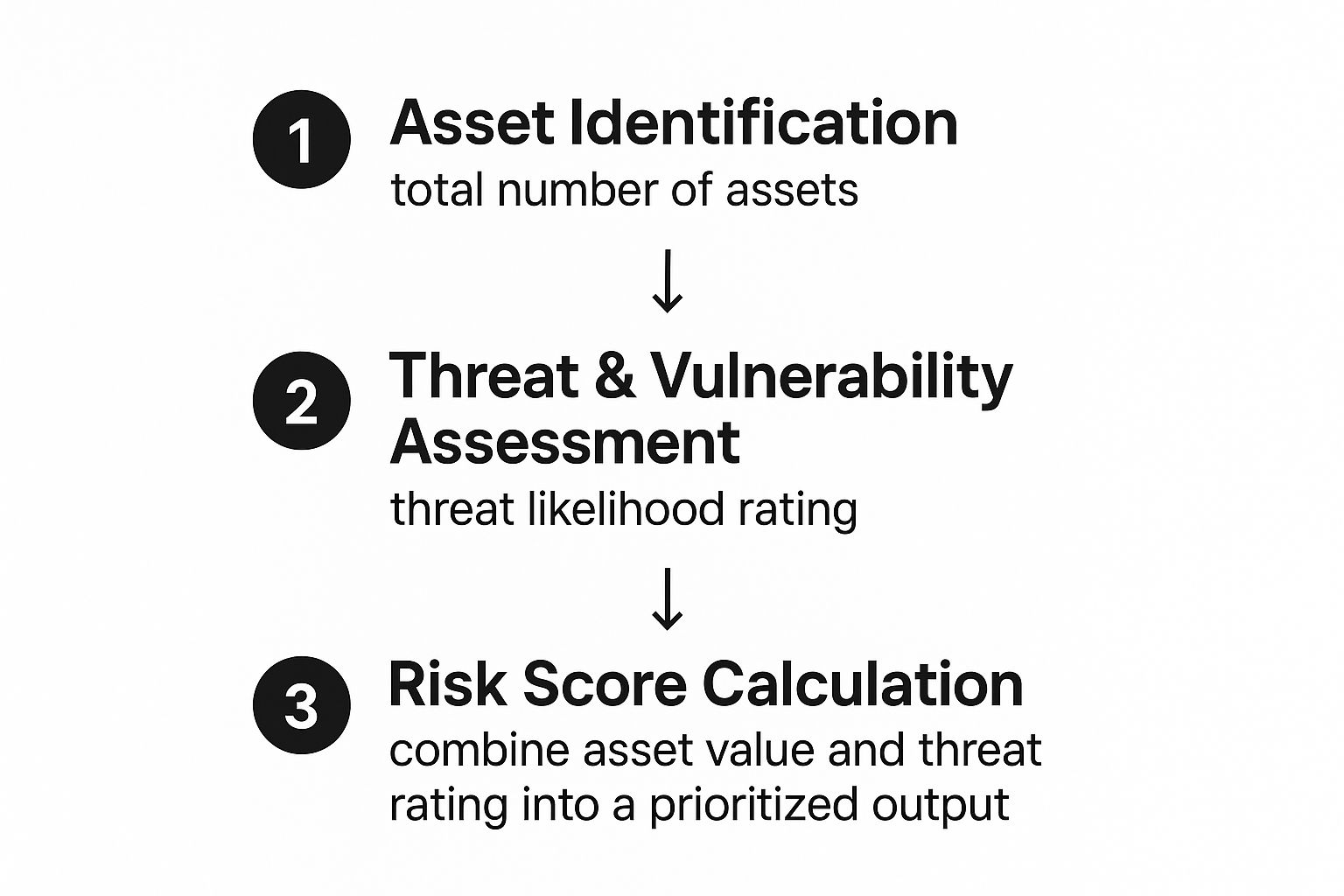
The key takeaway here is that your risk score is not some arbitrary number; it is the direct output of the foundational work you have already done. It turns your inventory and analysis into a prioritised to-do list.
For organisations that need a more granular, quantitative approach, there are established frameworks out there. In Australia, for instance, you can look at models like the ISS Cyber Risk Score. This score, ranging from 300 (high risk) to 850 (low risk), aims to predict the likelihood of a major cyber incident in the next 12 months by analysing a company's external security posture. You can read more about how these scores assess Australian companies to get a feel for it.
The objective is not just to create a long list of problems. It is to build a prioritised plan that directs your limited resources—time, money, and people—towards the threats that pose the greatest danger to your organisation's survival and success.
Ultimately, whether you stick with a simple qualitative matrix or dive into a detailed quantitative model, the principle is the same. A well-executed cybersecurity risk assessment template must end with a prioritised action plan. This methodical approach ensures you are not just busy with security tasks; you are actively reducing the most significant risks first, maximising your security investment and building genuine resilience.
Implementing Controls and Maintaining a Security Rhythm

A risk assessment that just sits on a shelf collecting dust is completely useless. Its real power is in the action it drives, turning that prioritised list of risks into real-world security improvements. This is where you shift gears from analysis to defence, putting security controls in place to tackle the specific threats you have uncovered.
Good security is never about a single, magic-bullet solution. It is all about layering different types of controls to build a defence that is robust and has depth. This layered approach means that if one control fails or gets bypassed, there is another one right behind it to stop a potential incident in its tracks.
I find it helpful to think about controls in three distinct categories:
- Preventative Controls: These are your front-line defences, designed to stop an incident before it can even start. Think advanced endpoint protection on all devices, strict access control policies, and mandatory security awareness training for all your staff.
- Detective Controls: These are your alarm systems. Their job is to spot malicious activity as it happens, or very shortly after. This includes continuous security monitoring of your network, intrusion detection systems, and even regular internal audits.
- Corrective Controls: When an incident inevitably happens, these are the measures that limit the damage and get you back on your feet. A well-rehearsed incident response plan and comprehensive data backup systems are the classics here for a reason.
Establishing a Continuous Security Cycle
Cybersecurity is not a "set and forget" project. The threat landscape, your own business operations, and the technology you rely on are all in a constant state of flux. That means your risk assessment has to be a living process, not a one-time event. Establishing a consistent rhythm for review is absolutely non-negotiable if you want to maintain a strong security posture.
Your first risk assessment provides a baseline—a snapshot in time. The real work is in treating it as a continuous cycle of review, refinement, and improvement. This is how you build genuine, long-term resilience.
A practical schedule keeps the whole process from feeling overwhelming and makes sure your defences evolve alongside new challenges. For most organisations, a full, comprehensive review once a year is a solid starting point. But you will want to supplement that with more frequent, targeted updates. For deeper insights on building a strong security function, it is worth understanding the benefits of hiring a data-driven cybersecurity team to manage this cycle.
A Practical Review and Update Schedule
Here is a sample rhythm you can adapt for your organisation. The goal is to keep your cybersecurity risk assessment template relevant and effective over the long haul.
| Review Type | Frequency | Triggers and Focus |
|---|---|---|
| Full Assessment | Annually | A complete, top-to-bottom reassessment of all assets, threats, vulnerabilities, and controls. |
| Quarterly Check-ins | Quarterly | Review high-priority risks, check progress on mitigation plans, and discuss any new, significant threats that have emerged. |
| Ad-Hoc Reviews | As needed | Triggered by major events like launching a new product, adopting a new cloud platform, or after a significant security incident. |
This kind of structured rhythm ensures your security efforts stay aligned with your business goals and are ready to handle the ever-changing nature of cyber threats. By treating risk assessment as an ongoing cycle, you turn it from a static document into the very engine of your proactive security strategy.
Answering Your Top Questions About Risk Assessment Templates
Even with the best template in hand, you are bound to run into a few questions when you start putting it all into practice. Let us tackle some of the most common queries I hear from teams diving into their first major cybersecurity risk assessment.
How Often Should We Actually Do This?
Look, a risk assessment is not a "set it and forget it" task. Things change too quickly for that. While a major, deep-dive assessment should be on the calendar at least annually, that is just the baseline.
Think of the annual review as your big-picture strategy session. But to stay ahead of the game, you need a more agile approach. I always recommend quarterly check-ins to review your highest-priority risks and see how your mitigation efforts are tracking.
Beyond that, you absolutely must trigger a fresh review any time there is a significant shift in your environment. These events are non-negotiable triggers for an immediate assessment:
- Rolling out a new, business-critical system (like a new CRM or ERP).
- Moving a big chunk of your infrastructure to a different cloud provider.
- After a major security incident—you need to understand exactly how it happened and plug the gaps.
Who Needs to Be in the Room?
One of the biggest mistakes I see is organisations treating risk assessment as a siloed IT problem. If it is just your tech team in a room, you are going to miss the plot completely. The process must be collaborative to be effective.
While your IT and security people will naturally lead the charge, they need input from others to get the full picture.
Here is who you need to involve:
- IT and Security Teams: These are your technical experts. They understand the threats, can spot the vulnerabilities, and know what controls are possible.
- Business Unit Leaders: These are the people who can tell you what an asset is actually worth to the business. They understand the real-world operational impact if a system goes down.
- Senior Management: Getting the leadership team involved ensures the whole exercise aligns with the company's strategic goals and, crucially, that you get the budget you need to fix things.
Without this mix of perspectives, you will end up with a technically sound assessment that completely misjudges the business impact of a threat.
What is the Difference Between Qualitative and Quantitative Assessments?
This one comes up a lot. Deciding which approach to take really depends on your organisation's maturity and what you are trying to achieve. Often, a blend of both works best.
A qualitative assessment is all about using descriptive scales—think 'High', 'Medium', and 'Low'—to rate and prioritise risks. It is a faster, more straightforward way to get a bird's-eye view of your risk profile without getting bogged down in complex maths. It is the perfect starting point.
A quantitative assessment, on the other hand, puts hard numbers on risk, usually in dollar figures. It is designed to answer questions like, "What is the annual loss expectancy if this server gets hit with ransomware?" This method is far more complex and needs a lot of data, but it gives you a powerful financial argument for investing in security.
My advice? Start with a qualitative assessment to quickly identify your biggest, scariest risks. Once you have that shortlist, you can apply a more rigorous quantitative analysis to those top threats to build a rock-solid business case for your mitigation plan.
Ultimately, a well-run risk assessment is not just about finding problems; it is about building a more resilient organisation. This requires a team with a broad range of abilities. To learn more, check out our guide on the top skills to look for in a cybersecurity professional.
At Redwolf Rosch, we connect Australian organisations with the elite IT and cybersecurity talent they need to thrive. If you are looking for a trusted recruitment partner to help you build out your security team, get in touch for an introductory chat today at https://redwolfrosch.com.au.
 Submit CV
Submit CV Submit vacancy
Submit vacancy  Call for a Candidate
Call for a Candidate